---
layout: default
title: Black Hat
---
> by Anthony Lawn
A game about an 80s blackhat hacker for hire who plans and executes feats of social engineering to attack the largest business conglomerates in the world.
#### Concept
The player uses their trusty computer to surveil target corporations. With knowledge in hand they proceed to plan an adventure-style mission to infiltrate and attack the corporation and take it down. Missions have no failure state and the outcomes of each mission guide the rest of the game and its story towards one of many endings.
#### Gameplay
Use a terminal to get money or perform surveillance on the target organization. With this information you plan missions against the corporation. While still at home you switch between various applications (a terminal, web browser, IRC, and a notepad) the latter of which lists the knowledge you've discovered. The general UI is a computer in the middle, a whiteboard where you make the decisions about the mission on the left, and a door (to actually perform the mission) on the right. As you discover more information more options can become available to you on the whiteboard. Once you lock in your decisions(exit through the door) a cutscene plays, with your chosen options directing the scene and its outcome. The mission will have some amount of success that affects the rest of the missions (and can cause characters to recur or become suspicious or other things). Note that "failing" a mission does NOT end the game, just gives the player a different story than if they had succeeded. The final ending is determined by the success of the last mission, with some potential flavor text determined by extreme success/failure in previous missions. Each ending should feel complete, and conclusive. Indeed, the whole game should have a sense of ambiguity to the point where it isn't even clear what endings are "good" or "bad".
Coincidentally, a recent indie game named "Orwell" happens to show pretty much exactly the data gathering mechanic I had envisioned. You can look through different web pages, (irc) chat logs, and peoples' filesystems and look for clues to put on your posterboard.
For example, the first mission would be all about gathering more information about the corporation. You could decide whether to use a rubber ducky or a wifi pineapple, etc. You could choose to just drop the device where someone will/won't find it (depending on the device), or whether to attempt infiltration through social engineering. Maybe one set of options would get a rubber ducky confiscated and plugged into a security terminal, allowing more of the info gathering script to succeed than it would on a normal employee's terminal. These outcomes could make certain characters become suspicious of you, get in trouble with management, etc., and also determine what pieces of information you can use later on for researching the company (e.g. whether you can access their network).
Certain interactions while researching (such as talking on IRC) may also influence how the missions will go. These are not decisions you make while planning, but rather consequences incurred whilst in the planning stage.
To give an example of an ending that doesn't feel like a failure while still not being the expected "true" ending (even though no ending will be the "right"/"true" ending) is if the protagonist actually determines the corporation is doing good, and the person who hired you is the real villain.
#### Aesthetic
The game will take place in the 80s, with dark or faded colors, especially faded gold. A good reference point would be the [Halt and Catch Fire](https://www.google.com/search?tbm=isch&q=halt+and+catch+fire+scene) or, to a lesser extent, [Mr.Robot](https://www.google.com/search?tbm=isch&q=mr+robot+scene) aesthetic. Try to include references to [1980s hackers](https://en.wikipedia.org/wiki/Timeline_of_computer_security_hacker_history#1980s) or other things that make it feel more authentically 80s.
  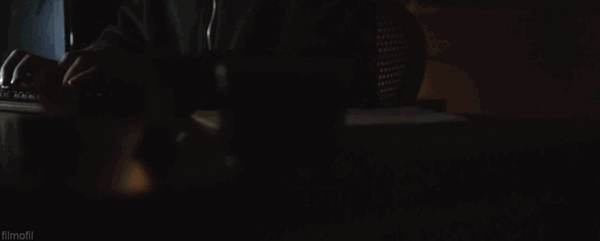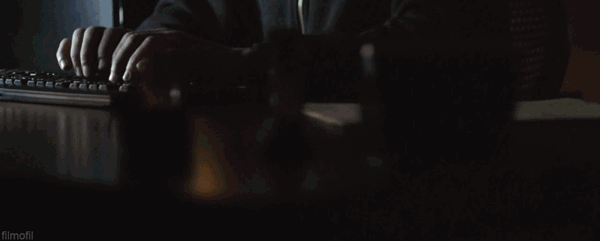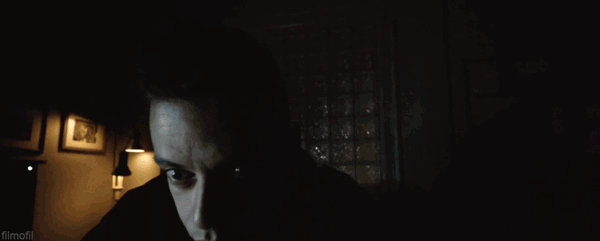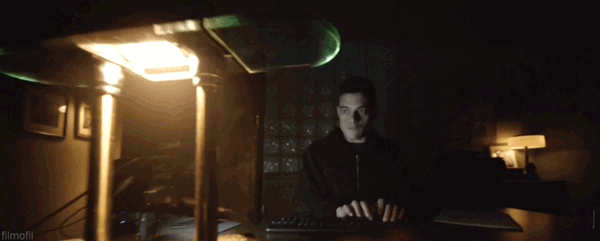



The atmosphere is filled with ambiguity and paranoia. Worries about making too big a splash as just a kid. Gets threats from people on IRC, maybe on one day before going to a mission someone comes to his house looking for him, etc.
#### Protagonist
The main character is an infamous "hacker for hire", very cynical of the society he's in, and actually likes taking jobs against large companies that are ingrained in society. His name is "Kim Swartz", a reference to Aaron Swartz (but without a gender ambiguous name, which helps with the whole "one person many faces" idea. The character should take inspiration from [Julian Assange](https://en.wikipedia.org/wiki/Julian_Assange), [Aaron Swartz](https://en.wikipedia.org/wiki/Aaron_Swartz), or maybe even [Kim Dotcom](https://en.wikipedia.org/wiki/Kim_Dotcom) (do note I'm not saying those were good people or that this protagonist is either, or implying that any of them were blackhat hackers. Just I think they'd have similar values- pro free speech, transparency, consumer rights, etc.).
Kim Swartz has high functioning dissociative identity disorder. Specifically, they picture mental switches that they can switch on and off, representing the different personalities they put on to help with social engineering. This can be used as justification for why Kim can't make decisions during the cutscene- once he's flipped the switch, he's on autopilot. During some paths he may become more mentall unstable and less able to control his disorder, and end up finding out things like some "other hackers" he thought were trying to stop him, were actually himself on different accounts. There could be events like the character finding other people on the internet claiming to have done the things he has done, or finding notes he doesn't remember writing (which could also lead him to suspecting carbon monoxide poisoning, leaning into the paranoia motif).